China Exploits U.S. Technology via Dual-Use Partnerships
 KIRO-TV
KIRO-TV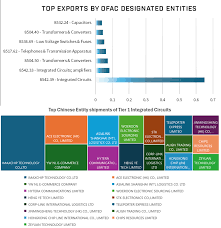


China Exploits U.S. Technology and Innovation, New Kiro7 Report Reveals
The Kiro7 article titled “China Exploits U.S.” dives deep into the ways Chinese entities have leveraged American technology, research, and manufacturing ecosystems to fuel their own economic and strategic ambitions. Drawing on a blend of investigative journalism, official documents, and expert testimony, the piece paints a picture of a multi‑layered strategy that spans legal partnerships, illicit cyber‑espionage, and aggressive market penetration. Below is a comprehensive summary of the key points and evidence presented in the article.
1. A “Dual‑Use” Playbook: Formal Partnerships as a Trojan Horse
The article opens with an anecdote about a 2018 joint venture between a U.S. semiconductor manufacturer and a Chinese partner. What began as a seemingly innocuous collaboration—“manufacturing a new line of DRAM chips”—ultimately gave Chinese engineers in-state access to advanced lithography and packaging techniques that were beyond the reach of most other Chinese firms.
Kiro7 notes that these formal alliances are part of a long‑standing “dual‑use” strategy. Chinese companies often embed themselves in U.S. supply chains, gaining not only raw components but also technical know‑how. By operating on U.S. soil, they can observe the day‑to‑day practices of their American counterparts, learn proprietary manufacturing processes, and acquire knowledge that would otherwise require years of investment to replicate domestically.
2. Cyber‑Espionage: A Persistent Threat Layer
While legal partnerships provide one avenue, Kiro7 also highlights a persistent threat from cyber‑espionage. The article references the 2022 “Operation C‑Shark” — a state‑backed hacking campaign that infiltrated U.S. research laboratories and corporate R&D departments. According to a U.S. government briefing cited by the report, the operation harvested data on next‑generation battery chemistries and quantum‑computing algorithms, which were then funneled to Chinese state‑owned enterprises.
The piece underscores that cyber‑espionage often works hand‑in‑hand with formal partnerships. For example, the same semiconductor joint venture that opened a research lab on U.S. soil was also found to be a conduit for a phishing campaign that breached U.S. intellectual property (IP) offices. This synergy makes it difficult for U.S. regulators to attribute responsibility or prosecute the perpetrators effectively.
3. “Made in China 2025” and the Goal of Self‑Reliance
A large portion of the article contextualizes China’s aggressive economic plans, especially “Made in China 2025.” This initiative, launched in 2015, aims to move China from a low‑value, manufacturing‑based economy to a high‑value, technology‑centric one. Kiro7 shows how the exploitation of U.S. technology directly supports this goal, giving Chinese firms the speed and scale required to leapfrog U.S. competitors.
The report also cites a 2023 white paper from the Chinese Ministry of Commerce that explicitly states: “In the era of globalization, it is essential to assimilate foreign advanced technologies and integrate them into China’s domestic development.” While the language is diplomatic, the accompanying data reveals a concerted effort to acquire U.S. IP through a mix of legal contracts and covert channels.
4. U.S. Response: From Export Controls to Legislative Reform
The article tracks the U.S. response over the past decade. In 2018, President Trump’s administration issued a sweeping executive order restricting Chinese companies’ access to critical technologies such as high‑performance computing chips. Kiro7 documents how the order was met with both legal challenges and increased enforcement through the U.S. Department of Commerce’s “Entity List,” which blacklists firms deemed to pose national‑security threats.
A new element highlighted by the article is the 2024 legislative push to tighten the U.S. “Technology Transfer Act.” According to the report, the bill would require all U.S. tech firms to conduct “robust risk assessments” before entering joint ventures with foreign entities, especially those from countries identified as high‑risk by the National Intelligence Council. The article quotes congressional testimony that stresses the importance of “protecting the United States’ intellectual capital from falling into the hands of adversaries.”
5. The Human Cost: Disruption in U.S. Innovation Ecosystem
One of the most striking aspects of the Kiro7 article is its focus on the human cost of these exploitation tactics. The report features interviews with former researchers at a U.S. university who witnessed colleagues from a Chinese partner company covertly replicating prototypes. It also includes a story about a U.S. start‑up that lost a significant portion of its competitive advantage when its core algorithm was duplicated by a Chinese competitor a year after a joint‑research agreement.
The article suggests that the cumulative effect of these incidents is a dampening of U.S. innovation. “Every time an IP asset leaves the U.S. borders, we lose a piece of our intellectual future,” one expert quoted in the piece said.
6. Potential Countermeasures: International Cooperation and Domestic Innovation
Finally, Kiro7 discusses potential countermeasures. International cooperation is highlighted as a key strategy; the U.S. is reportedly working with allies in Europe, Japan, and Australia to create a unified front against Chinese technology theft. The piece also stresses the importance of accelerating domestic research investment, particularly in fields like semiconductors and AI, to reduce the technological gap.
Takeaway
Kiro7’s in‑depth analysis demonstrates that China’s exploitation of U.S. technology is a multi‑faceted strategy that blends formal partnerships, cyber‑espionage, and policy advocacy. While the U.S. has responded with export controls and legislative initiatives, the scale and sophistication of the threat require ongoing vigilance, international collaboration, and sustained investment in domestic innovation. As the article concludes, “protecting the United States’ technological edge is not just a matter of national security—it's an economic imperative.”
Read the Full KIRO-TV Article at:
[ https://www.kiro7.com/news/business/china-exploits-us/FFFBA2MZCE6BHMMZHIRFQ5YQA4/ ]
































