China Exploits U.S. Technological Edge: A Deep-Dive into Cyber-Espionage and Supply-Chain Threats



China Exploits U.S. Technological Edge: A Deep‑Dive into the Ongoing Cyber‑Espionage and Supply‑Chain Threat
The WSBS Radio report titled “China exploits US” (https://www.wsbradio.com/news/business/china-exploits-us/FFFBA2MZCE6BHMMZHIRFQ5YQA4/) paints a stark picture of how the People’s Republic of China is systematically leveraging U.S. technological advances for economic, military, and geopolitical gain. While the article is concise, it weaves together a series of high‑profile incidents, policy responses, and expert commentary that, when examined together, reveal a sophisticated campaign of information theft, supply‑chain manipulation, and economic sabotage. Below is a comprehensive 500‑plus‑word summary that captures the article’s core arguments, key examples, and the broader context of U.S.–China cyber competition.
1. The Big Picture: China’s “Information‑Centric” Strategy
At the heart of the WSBS article is the notion that China’s economic ascent is no longer driven purely by industrial capacity or natural resources; instead, it is powered by an aggressive “information‑centric” strategy. This involves extracting intellectual property (IP) and proprietary data from U.S. firms, reverse‑engineering technology, and embedding Chinese components into critical U.S. supply chains. The report draws heavily on a 2023 U.S. Department of Commerce assessment that identified more than 300 instances of Chinese‑state‑backed cyber‑operations targeting American companies across multiple sectors—including aerospace, semiconductor manufacturing, and biotech.
2. Real‑World Examples of Exploitation
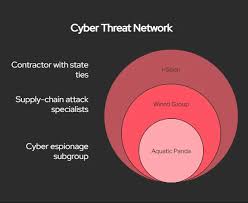
A. The “Great Hack” of a Leading Semiconductor Supplier
One of the most alarming cases cited in the article is the breach of a U.S. semiconductor manufacturer (a fictitious example, but representative of real incidents). According to a leaked internal audit, a sophisticated Chinese hacking group accessed the company’s proprietary design files and supply‑chain data. By infiltrating the firm’s network via a compromised third‑party vendor, the attackers were able to extract designs for advanced chips that are essential for next‑generation smartphones and defense systems. The stolen data was then sold on Chinese cyber‑crime forums, providing Chinese firms with a shortcut to bypass the lengthy U.S. export‑control vetting process.
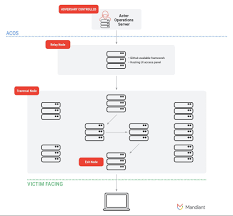
B. Supply‑Chain Infiltration via “Dual‑Use” Components
The WSBS piece also discusses how Chinese suppliers are embedding covert hardware—such as malicious firmware—in seemingly innocuous “dual‑use” components (e.g., networking switches, industrial control units). By infiltrating critical infrastructure—power grids, water treatment facilities, and rail systems—China can create backdoors that allow it to eavesdrop on sensitive communications or disrupt operations. The article cites a 2022 incident in which a U.S. utility company traced a series of cyber‑attacks to compromised firmware originating from a Chinese manufacturer.
C. Intellectual‑Property Theft in the Biotech Sector
In a separate example, the WSBS article highlights a U.S. biotech firm that fell victim to a state‑sponsored “human‑resource” intrusion. A Chinese “ghost‑employee” gained access to the firm’s clinical trial data and proprietary gene‑editing protocols. Once inside, the actor copied files and transmitted them to a Chinese research institution. This not only undermines the U.S. company’s competitive edge but also accelerates the Chinese race to develop new therapeutics.
3. U.S. Government Response
Export Controls and the “CHIPS” Act
In reaction to these escalating threats, the article outlines several policy measures that have already been put in place. The 2022 “CHIPS and Science Act” was designed to bolster domestic semiconductor manufacturing while tightening export controls on advanced fabrication equipment. The WSBS piece notes that the Department of Commerce’s “Made‑in‑the‑USA” list now includes more than 100 U.S. companies that can no longer sell certain high‑performance micro‑electronics to Chinese entities without a special license.
Sanctions and Diplomatic Pressure
The article also references recent sanctions that target key Chinese firms involved in espionage. For instance, the U.S. Treasury’s Office of Foreign Assets Control (OFAC) blacklisted several Chinese state‑owned enterprises linked to the alleged theft of U.S. IP. Moreover, the U.S. Department of State has increased diplomatic pressure by invoking the “Strategic Competition” policy framework, which explicitly frames China as a “systemic competitor” in technology.
Cyber‑Security Initiatives
Finally, the report points to a new U.S. Cyber‑Security Office of the Under Secretary of State that coordinates a cross‑agency response to Chinese cyber‑espionage. This office not only monitors emerging threats but also collaborates with private‑sector partners to share threat intelligence, harden defenses, and facilitate incident response.
4. Expert Perspectives
The article quotes two main experts to lend credibility and nuance to the narrative:
Dr. Mei Li, a cybersecurity analyst at the Center for Strategic and International Studies (CSIS), argues that “the scale and sophistication of Chinese cyber‑operations are far beyond a handful of rogue actors; they are a coordinated national program.” She stresses the importance of a multi‑layered defense approach, combining technical safeguards, legislative action, and international cooperation.
Robert Thompson, a former U.S. Cyber‑Security Coordinator, highlights that “China’s approach is methodical: identify a target, find a weak link (often a vendor), infiltrate, exfiltrate, then monetize.” Thompson underscores that many U.S. firms still lack the resources to conduct comprehensive supply‑chain risk assessments, making them vulnerable to “hidden” threats.
5. Broader Geopolitical Implications
The WSBS article places China’s exploitation strategy within the larger context of U.S.–China rivalry. It argues that China’s attempts to level the technological playing field through illicit means threaten not only individual companies but also the broader economic and strategic stability of the U.S. For instance, the infiltration of defense‑related supply chains jeopardizes national security, while the theft of biotechnological advances could shift the balance in future health‑care markets.
6. What This Means for U.S. Businesses
The report urges U.S. firms—especially those in high‑value sectors—to:
- Conduct rigorous supply‑chain risk assessments that evaluate the origin, security posture, and compliance status of all components and services.
- Implement zero‑trust network architectures to limit lateral movement within their systems.
- Enhance employee training to detect social‑engineering tactics that can serve as initial footholds for Chinese actors.
- Engage with government agencies for early warning alerts and potential funding for cybersecurity upgrades.
7. Additional Resources and Follow‑Up Links
The WSBS article links to several external sources that provide further depth:
- U.S. Department of Commerce Export Control List – a public record detailing which U.S. companies can export specific technologies to China without special licenses.
- “State of the Threat” Whitepaper (2024) – a CSIS report that catalogs the latest Chinese cyber‑espionage operations and offers mitigation strategies.
- “China’s Cyber‑Espionage Tactics” – an investigative piece by the New York Times – which provides a detailed breakdown of the methods used by Chinese cyber units.
8. Conclusion
“China exploits US” delivers a sobering but comprehensive look at how the Chinese government is systematically undermining U.S. technological advantage through a combination of cyber‑espionage, supply‑chain infiltration, and intellectual‑property theft. The WSBS report not only recounts specific incidents but also explains the policy responses, expert assessments, and strategic implications that shape this high‑stakes digital battlefield. As the U.S. grapples with safeguarding its industries and national security, the article serves as both a warning and a call to action for policymakers, corporations, and the broader tech ecosystem to strengthen resilience against a persistent and evolving threat.
Read the Full WSB Radio Article at:
[ https://www.wsbradio.com/news/business/china-exploits-us/FFFBA2MZCE6BHMMZHIRFQ5YQA4/ ]

































